STSのエンドポイントを .aws/config で指定する方法。
- .~/aws/config
[profile dev] services = custom-endpoint [services custom-endpoint] s3 = endpoint_url = sts = endpoint_url =
$ aws s3 ls --profile s3_access --endpoint-url https://bucket.vpce-********.s3.ap-northeast-1.vpce.amazonaws.com s3://s3-data-prod-********-ap-northeast-1 --debug ... File "/usr/lib/python3.9/site-packages/urllib3/connection.py", line 174, in _new_conn raise ConnectTimeoutError( urllib3.exceptions.ConnectTimeoutError: (<botocore.awsrequest.AWSHTTPSConnection object at 0x7f9469a838b0>, 'Connection to sts.amazonaws.com timed out. (connect timeout=60)')
$ aws ... --debug
$ telnet https://bucket.vpce-********.s3.ap-northeast-1.vpce.amazonaws.com 443
$ telnet https://vpce-********-********.sts.ap-northeast-1.vpce.amazonaws.com 443
$ aws sts get-caller-identity --endpoint-url https://vpce-********-********.sts.ap-northeast-1.vpce.amazonaws.com --debug ... 2024-08-01 16:03:40,713 - MainThread - urllib3.connectionpool - DEBUG - Starting new HTTPS connection (3): vpce-********-********.sts.ap-northeast-1.vpce.amazonaws.com:443 ... Connect timeout on endpoint URL: "https://vpce-********-********.sts.ap-northeast-1.vpce.amazonaws.com/"
AWS CLI で IAM ユーザーのクレデンシャルで認証して、スイッチロールして S3 にアクセスする設定。
$ aws s3 ls --profile s3_access --endpoint-url https://bucket.vpce-********-********.s3.ap-northeast-1.vpce.amazonaws.com
2024-07-31 05:05:46,977 - MainThread - urllib3.connectionpool - DEBUG - Starting new HTTPS connection (2): sts.ap-northeast-1.amazonaws.com:443
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "sts:AssumeRole" ], "Resource": [ "arn:aws:iam::123456789012:role/s3-upload-role" ] } ] }
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::123456789012:user/s3-upload-user" }, "Action": "sts:AssumeRole" } ] }
[profile s3_access] region = ap-northeast-1 role_arn = arn:aws:iam::123456789012:role/s3-upload-role source_profile=s3_access
[s3_access] aws_access_key_id = ******** aws_secret_access_key = ********
ここ数年自重トレーニングしてたけど、久しぶりにジムを再開したので、分割法をメモ。
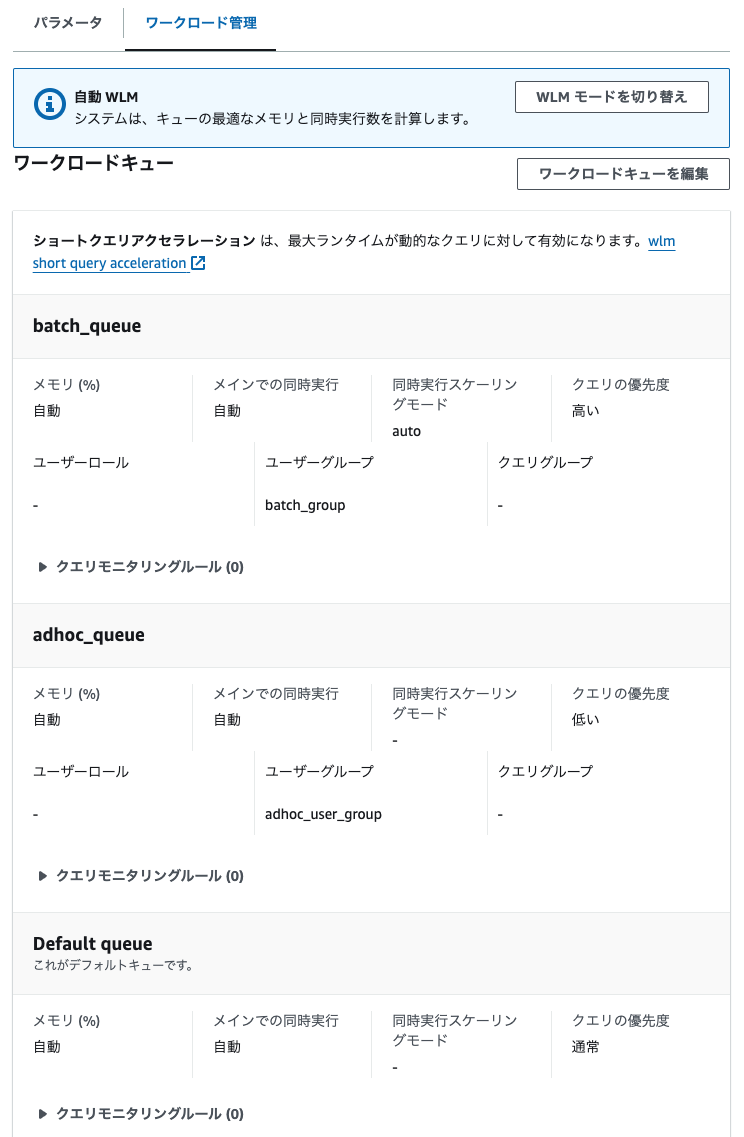
GRANT ROLE ロール名 TO ユーザー名create user ユーザー名 ... in group グループ名CREATE GROUP batch_group; CREATE GROUP adhoc_user_group;
# バッチユーザー CREATE USER batch_user_01 PASSWORD 'Password123!' IN GROUP batch_group; CREATE USER batch_user_02 PASSWORD 'Password123!' IN GROUP batch_group; # 個人ユーザー CREATE USER individual_user_01 PASSWORD 'Password123!' IN GROUP adhoc_user_group; CREATE USER individual_user_02 PASSWORD 'Password123!' IN GROUP adhoc_user_group;
create schema system_schema; create schema individual_schema;
CREATE TABLE system_schema.stg_tbl_01 (col1 VARCHAR(20)); # stg_tbl_01 CREATE TABLE system_schema.dwh_tbl_01 (col1 VARCHAR(20)); # dwh_tbl_01 CREATE TABLE individual_schema.wrk_tbl_01 (col1 VARCHAR(20)); # wrk_tbl_01 CREATE TABLE individual_schema.wrk_tbl_02 (col1 VARCHAR(20)); # wrk_tbl_02
# ロールを作成 CREATE ROLE system_role; CREATE ROLE individual_role;
# ロールからスキーマへの権限を付与 GRANT USAGE ON SCHEMA system_schema TO ROLE system_role; GRANT USAGE ON SCHEMA individual_schema TO ROLE individual_role; GRANT SELECT, INSERT, UPDATE, DELETE ON ALL TABLES IN SCHEMA system_schema TO ROLE system_role; GRANT SELECT, INSERT, UPDATE, DELETE ON ALL TABLES IN SCHEMA individual_schema TO ROLE individual_role; # ユーザーにロール単位でアクセス権限を付与 GRANT ROLE system_role TO batch_user_01, batch_user_02; GRANT ROLE individual_role TO individual_user_01, individual_user_02;
dev=# SELECT * FROM svv_user_grants; user_id | user_name | role_id | role_name | admin_option ---------+----------------------------------------------------+---------+-----------------+-------------- 181 | dm_admin_user | 372701 | dm_admin_role | f 189 | ds:central_db_nsp_b77f35248f9446f9bc61b7d8a3026df5 | 871650 | ds:central_db | f 190 | batch_user_01 | 1157704 | system_role | f 191 | batch_user_02 | 1157704 | system_role | f 190 | batch_user_01 | 1157705 | individual_role | f 192 | individual_user_01 | 1157705 | individual_role | f 193 | individual_user_02 | 1157705 | individual_role | f (7 rows)
[ec2-user@ip-172-31-0-101 ~]$ psql "host=redshift-cluster-poc-central.********.ap-northeast-1.redshift.amazonaws.com user=individual_user_01 dbname=dev port=5439" Password for user individual_user_01: psql (13.7, server 8.0.2) SSL connection (protocol: TLSv1.2, cipher: ECDHE-RSA-AES256-GCM-SHA384, bits: 256, compression: off) Type "help" for help. dev=> select * from system_schema.stg_tbl_01; ERROR: permission denied for schema system_schema dev=> select * from individual_schema.wrk_tbl_01; col1 ------ (0 rows) dev=>
CREATE ROLE role_name
[ EXTERNALID external_id ]
CREATE GROUP group_name [ [ WITH ] [ USER username ] [, ...] ]
CREATE USER name [ WITH ] PASSWORD { 'password' | 'md5hash' | 'sha256hash' | DISABLE } [ option [ ... ] ] where option can be: CREATEDB | NOCREATEDB | CREATEUSER | NOCREATEUSER | SYSLOG ACCESS { RESTRICTED | UNRESTRICTED } | IN GROUP groupname [, ... ] | VALID UNTIL 'abstime' | CONNECTION LIMIT { limit | UNLIMITED } | SESSION TIMEOUT limit | EXTERNALID external_id
GRANT ROLE role1 TO reguser; GRANT ROLE role2 TO reguser; GRANT ROLE role1 TO superuser; GRANT ROLE role2 TO superuser; SELECT user_name,role_name,admin_option FROM svv_user_grants; user_name | role_name | admin_option -----------+-----------+-------------- superuser | role1 | False reguser | role1 | False superuser | role2 | False reguser | role2 | False