Active Directory(AD)連携でAWSマネジメントコンソールにログインしてさらに別のAWSアカウントにスイッチロールして操作した場合、同じADユーザー(AWSでは同じロール)を同時に複数人で操作した場合に誰が何をしたか追跡できるか調べたメモ。
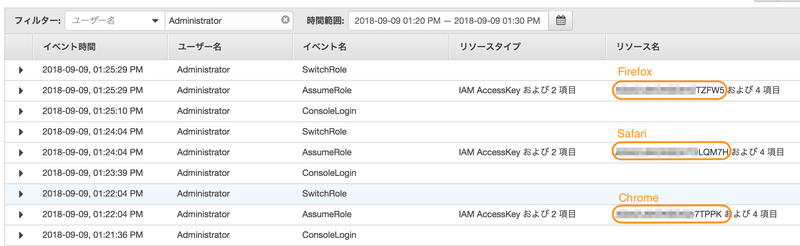
Chrome、Safari、Firefox で同時にログインして S3 バケットを作成し、CloudTrail から誰が何をしたかどこまで追跡できるか確認した。
以下ではアカウント1のIDを「100000000000」、アカウント2を「200000000000」として、アカウント1にAD連携でログインしてアカウント2にスイッチロールしている。
準備
- AWSアカウントを2つ作成する
- AD連携でのマネジメントコンソールログイン設定
- クロスアカウントでのスイッチロール設定
アカウント2にスイッチロールしてS3バケットを作成する
chrome から S3 バケット作成
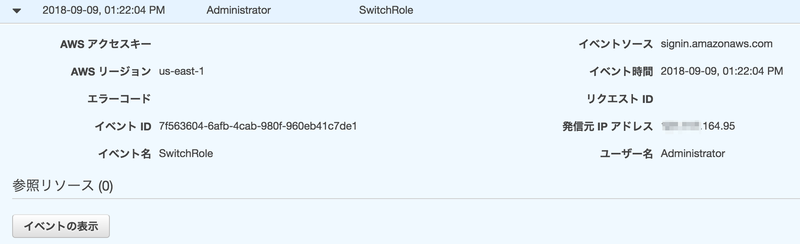
- SwitchRole
{ "eventVersion": "1.05", "userIdentity": { "type": "AssumedRole", "principalId": "A***************MOF2Y:Administrator", "arn": "arn:aws:sts::200000000000:assumed-role/az2AdminRole/Administrator", ★az2AdminRole にスイッチロール "accountId": "200000000000" }, "eventTime": "2018-09-09T04:22:04Z", "eventSource": "signin.amazonaws.com", "eventName": "SwitchRole", ★スイッチロール "awsRegion": "us-east-1", "sourceIPAddress": "***.***.164.95", "userAgent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.106 Safari/537.36", ★Chrome でアクセス "requestParameters": null, "responseElements": { "SwitchRole": "Success" }, "additionalEventData": { "SwitchFrom": "arn:aws:sts::100000000000:assumed-role/AdminRole/Administrator", ★AWSアカウント1からスイッチロール "RedirectTo": "https://console.aws.amazon.com/console/home" }, "eventID": "7f563604-6afb-4cab-980f-960eb41c7de1", "eventType": "AwsConsoleSignIn", "recipientAccountId": "200000000000" }
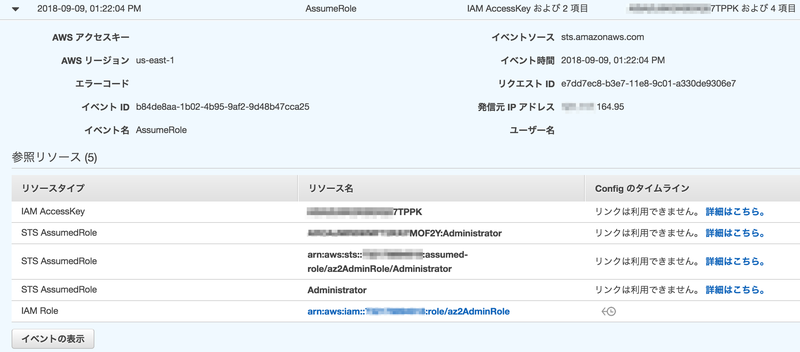
- AssumeRole
{ "eventVersion": "1.05", "userIdentity": { "type": "AWSAccount", "principalId": "****************5PT7S:Administrator", "accountId": "100000000000" }, "eventTime": "2018-09-09T04:22:04Z", "eventSource": "sts.amazonaws.com", "eventName": "AssumeRole", "awsRegion": "us-east-1", "sourceIPAddress": "***.***.164.95", "userAgent": "aws-internal/3", "requestParameters": { "roleArn": "arn:aws:iam::200000000000:role/az2AdminRole", "roleSessionName": "Administrator" }, "responseElements": { "credentials": { "accessKeyId": "A**************7TPPK", ★アカウント1と紐付けできる "expiration": "Sep 9, 2018 5:22:04 AM", "sessionToken": ".../ijsv9LcBQ==" }, "assumedRoleUser": { "assumedRoleId": "A***************MOF2Y:Administrator", "arn": "arn:aws:sts::200000000000:assumed-role/az2AdminRole/Administrator" } }, "requestID": "e7dd7ec8-b3e7-11e8-9c01-a330de9306e7", "eventID": "b84de8aa-1b02-4b95-9af2-9d48b47cca25", "resources": [ { "ARN": "arn:aws:iam::200000000000:role/az2AdminRole", "accountId": "200000000000", "type": "AWS::IAM::Role" } ], "eventType": "AwsApiCall", "recipientAccountId": "200000000000", "sharedEventID": "62d3f672-c89e-4ed6-b29a-07d79938c8df" }
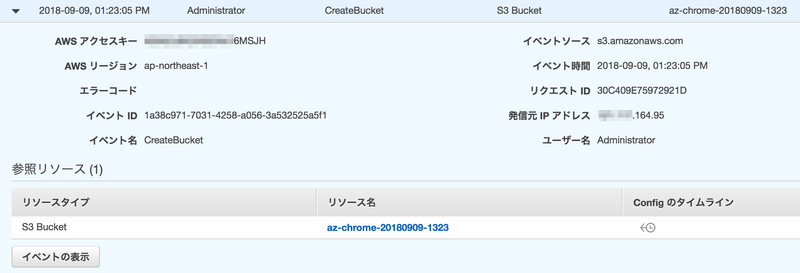
- CreateBucket
{ "eventVersion": "1.05", "userIdentity": { "type": "AssumedRole", "principalId": "A***************MOF2Y:Administrator", "arn": "arn:aws:sts::200000000000:assumed-role/az2AdminRole/Administrator", "accountId": "200000000000", "accessKeyId": "A**************6MSJH", ★この accessKeyId で他のセッションと区別できるが、どのセッションから SwitchRole したかは紐付けできない "sessionContext": { "attributes": { "mfaAuthenticated": "false", "creationDate": "2018-09-09T04:22:04Z" }, "sessionIssuer": { "type": "Role", "principalId": "A***************MOF2Y", "arn": "arn:aws:iam::200000000000:role/az2AdminRole", "accountId": "200000000000", "userName": "az2AdminRole" } }, "invokedBy": "AWS Internal" }, "eventTime": "2018-09-09T04:23:05Z", "eventSource": "s3.amazonaws.com", "eventName": "CreateBucket", "awsRegion": "ap-northeast-1", "sourceIPAddress": "***.***.164.95", "userAgent": "[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.398 Linux/4.9.93-0.1.ac.178.67.327.metal1.x86_64 OpenJDK_64-Bit_Server_VM/25.181-b13 java/1.8.0_181]", "requestParameters": { "CreateBucketConfiguration": { "LocationConstraint": "ap-northeast-1", "xmlns": "http://s3.amazonaws.com/doc/2006-03-01/" }, "bucketName": "az-chrome-20180909-1323" }, "responseElements": null, "additionalEventData": { "vpcEndpointId": "vpce-8******6" }, "requestID": "30C409E75972921D", "eventID": "1a38c971-7031-4258-a056-3a532525a5f1", "eventType": "AwsApiCall", "recipientAccountId": "200000000000", "vpcEndpointId": "vpce-8******6" }
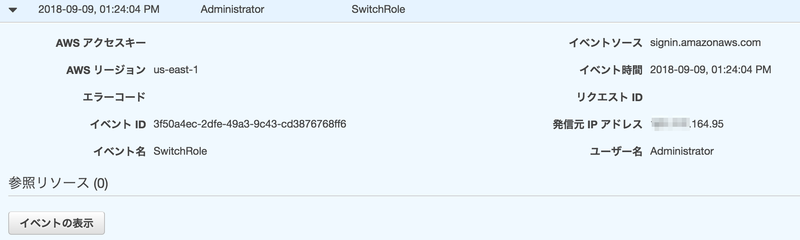
Safari
- SwitchRole
{ "eventVersion": "1.05", "userIdentity": { "type": "AssumedRole", "principalId": "A***************MOF2Y:Administrator", "arn": "arn:aws:sts::200000000000:assumed-role/az2AdminRole/Administrator", "accountId": "200000000000" }, "eventTime": "2018-09-09T04:24:04Z", "eventSource": "signin.amazonaws.com", "eventName": "SwitchRole", "awsRegion": "us-east-1", "sourceIPAddress": "***.***.164.95", "userAgent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/11.1.2 Safari/605.1.15", "requestParameters": null, "responseElements": { "SwitchRole": "Success" }, "additionalEventData": { "SwitchFrom": "arn:aws:sts::100000000000:assumed-role/AdminRole/Administrator", "RedirectTo": "https://console.aws.amazon.com/console/home" }, "eventID": "3f50a4ec-2dfe-49a3-9c43-cd3876768ff6", "eventType": "AwsConsoleSignIn", "recipientAccountId": "200000000000" }
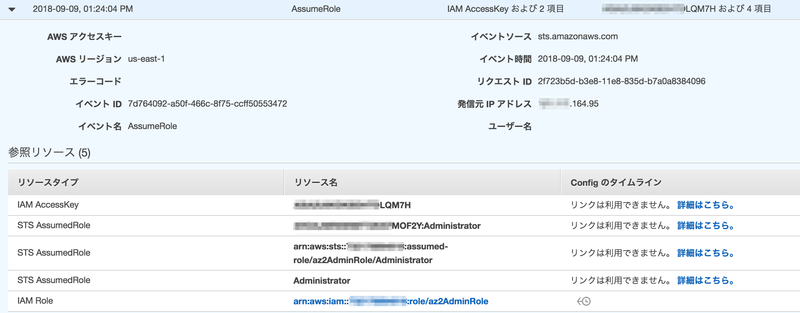
- AssumeRole
{ "eventVersion": "1.05", "userIdentity": { "type": "AWSAccount", "principalId": "****************5PT7S:Administrator", "accountId": "100000000000" }, "eventTime": "2018-09-09T04:24:04Z", "eventSource": "sts.amazonaws.com", "eventName": "AssumeRole", "awsRegion": "us-east-1", "sourceIPAddress": "***.***.164.95", "userAgent": "aws-internal/3", "requestParameters": { "roleArn": "arn:aws:iam::200000000000:role/az2AdminRole", "roleSessionName": "Administrator" }, "responseElements": { "credentials": { "accessKeyId": "A**************LQM7H", ★アカウント1と紐付けできる "expiration": "Sep 9, 2018 5:24:04 AM", "sessionToken": ".../jyjkwNLcBQ==" }, "assumedRoleUser": { "assumedRoleId": "A***************MOF2Y:Administrator", "arn": "arn:aws:sts::200000000000:assumed-role/az2AdminRole/Administrator" } }, "requestID": "2f723b5d-b3e8-11e8-835d-b7a0a8384096", "eventID": "7d764092-a50f-466c-8f75-ccff50553472", "resources": [ { "ARN": "arn:aws:iam::200000000000:role/az2AdminRole", "accountId": "200000000000", "type": "AWS::IAM::Role" } ], "eventType": "AwsApiCall", "recipientAccountId": "200000000000", "sharedEventID": "87809662-23c3-4761-84c8-ce6917aa2c82" }
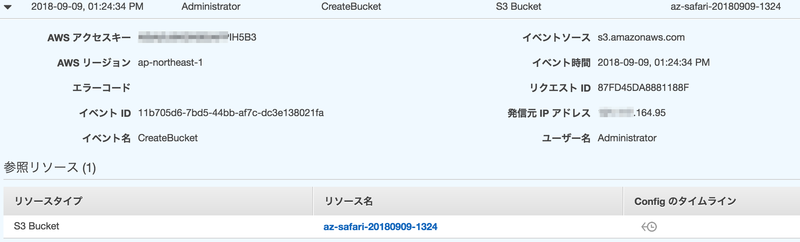
- CreateBucket
{ "eventVersion": "1.05", "userIdentity": { "type": "AssumedRole", "principalId": "A***************MOF2Y:Administrator", "arn": "arn:aws:sts::200000000000:assumed-role/az2AdminRole/Administrator", "accountId": "200000000000", "accessKeyId": "A**************IH5B3", ★この accessKeyId で他のセッションと区別できるが、どのセッションから SwitchRole したかは紐付けできない "sessionContext": { "attributes": { "mfaAuthenticated": "false", "creationDate": "2018-09-09T04:24:04Z" }, "sessionIssuer": { "type": "Role", "principalId": "A***************MOF2Y", "arn": "arn:aws:iam::200000000000:role/az2AdminRole", "accountId": "200000000000", "userName": "az2AdminRole" } }, "invokedBy": "AWS Internal" }, "eventTime": "2018-09-09T04:24:34Z", "eventSource": "s3.amazonaws.com", "eventName": "CreateBucket", "awsRegion": "ap-northeast-1", "sourceIPAddress": "***.***.164.95", "userAgent": "[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.398 Linux/4.9.93-0.1.ac.178.67.327.metal1.x86_64 OpenJDK_64-Bit_Server_VM/25.181-b13 java/1.8.0_181]", "requestParameters": { "CreateBucketConfiguration": { "LocationConstraint": "ap-northeast-1", "xmlns": "http://s3.amazonaws.com/doc/2006-03-01/" }, "bucketName": "az-safari-20180909-1324" }, "responseElements": null, "additionalEventData": { "vpcEndpointId": "vpce-8******6" }, "requestID": "87FD45DA8881188F", "eventID": "11b705d6-7bd5-44bb-af7c-dc3e138021fa", "eventType": "AwsApiCall", "recipientAccountId": "200000000000", "vpcEndpointId": "vpce-8******6" }
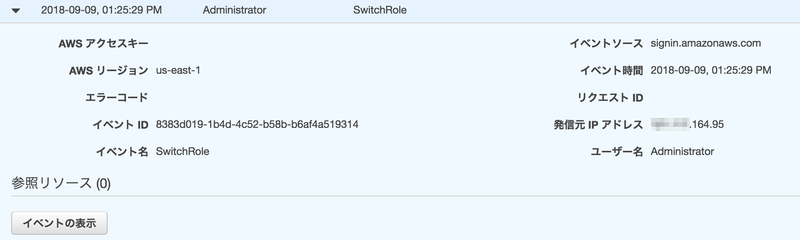
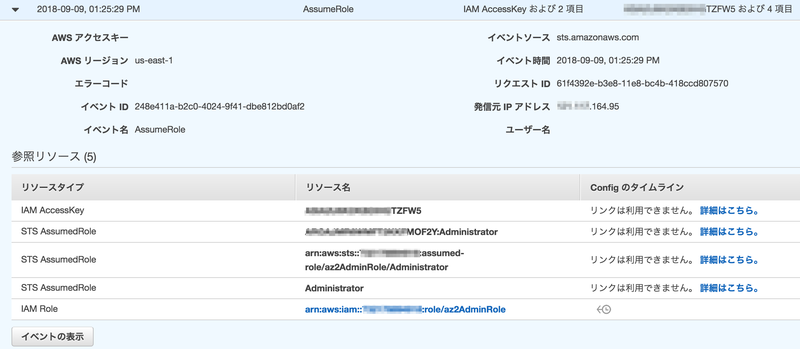
firefox
- SwitchRole
{ "eventVersion": "1.05", "userIdentity": { "type": "AssumedRole", "principalId": "A***************MOF2Y:Administrator", "arn": "arn:aws:sts::200000000000:assumed-role/az2AdminRole/Administrator", "accountId": "200000000000" }, "eventTime": "2018-09-09T04:25:29Z", "eventSource": "signin.amazonaws.com", "eventName": "SwitchRole", "awsRegion": "us-east-1", "sourceIPAddress": "***.***.164.95", "userAgent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:52.0) Gecko/20100101 Firefox/52.0", "requestParameters": null, "responseElements": { "SwitchRole": "Success" }, "additionalEventData": { "SwitchFrom": "arn:aws:sts::100000000000:assumed-role/AdminRole/Administrator", "RedirectTo": "https://console.aws.amazon.com/console/home" }, "eventID": "8383d019-1b4d-4c52-b58b-b6af4a519314", "eventType": "AwsConsoleSignIn", "recipientAccountId": "200000000000" }
- AssumeRole
{ "eventVersion": "1.05", "userIdentity": { "type": "AWSAccount", "principalId": "****************5PT7S:Administrator", "accountId": "100000000000" }, "eventTime": "2018-09-09T04:25:29Z", "eventSource": "sts.amazonaws.com", "eventName": "AssumeRole", "awsRegion": "us-east-1", "sourceIPAddress": "***.***.164.95", "userAgent": "aws-internal/3", "requestParameters": { "roleArn": "arn:aws:iam::200000000000:role/az2AdminRole", "roleSessionName": "Administrator" }, "responseElements": { "credentials": { "accessKeyId": "A***************TZFW5", ★アカウント1と紐付けできる "expiration": "Sep 9, 2018 5:25:29 AM", "sessionToken": "...ASi5wdLcBQ==" }, "assumedRoleUser": { "assumedRoleId": "A***************MOF2Y:Administrator", "arn": "arn:aws:sts::200000000000:assumed-role/az2AdminRole/Administrator" } }, "requestID": "61f4392e-b3e8-11e8-bc4b-418ccd807570", "eventID": "248e411a-b2c0-4024-9f41-dbe812bd0af2", "resources": [ { "ARN": "arn:aws:iam::200000000000:role/az2AdminRole", "accountId": "200000000000", "type": "AWS::IAM::Role" } ], "eventType": "AwsApiCall", "recipientAccountId": "200000000000", "sharedEventID": "57441f3f-bf33-4090-ae3b-d2febc1f6efd" }
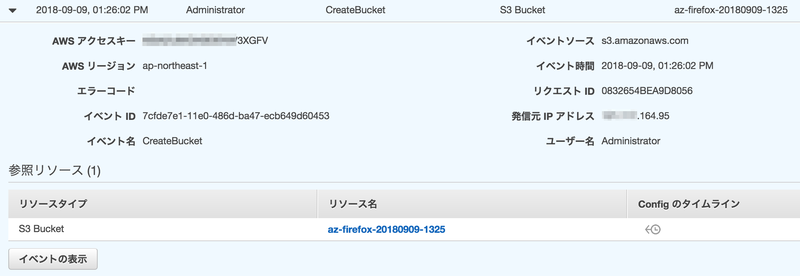
- CreateBucket
{ "eventVersion": "1.05", "userIdentity": { "type": "AssumedRole", "principalId": "A***************MOF2Y:Administrator", "arn": "arn:aws:sts::200000000000:assumed-role/az2AdminRole/Administrator", "accountId": "200000000000", "accessKeyId": "A**************3XGFV", ★この accessKeyId で他のセッションと区別できるが、どのセッションから SwitchRole したかは紐付けできない "sessionContext": { "attributes": { "mfaAuthenticated": "false", "creationDate": "2018-09-09T04:25:29Z" }, "sessionIssuer": { "type": "Role", "principalId": "A***************MOF2Y", "arn": "arn:aws:iam::200000000000:role/az2AdminRole", "accountId": "200000000000", "userName": "az2AdminRole" } }, "invokedBy": "AWS Internal" }, "eventTime": "2018-09-09T04:26:02Z", "eventSource": "s3.amazonaws.com", "eventName": "CreateBucket", "awsRegion": "ap-northeast-1", "sourceIPAddress": "***.***.164.95", "userAgent": "[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.398 Linux/4.9.93-0.1.ac.178.67.327.metal1.x86_64 OpenJDK_64-Bit_Server_VM/25.181-b13 java/1.8.0_181]", "requestParameters": { "CreateBucketConfiguration": { "LocationConstraint": "ap-northeast-1", "xmlns": "http://s3.amazonaws.com/doc/2006-03-01/" }, "bucketName": "az-firefox-20180909-1325" }, "responseElements": null, "additionalEventData": { "vpcEndpointId": "vpce-8******6" }, "requestID": "0832654BEA9D8056", "eventID": "7cfde7e1-11e0-486d-ba47-ecb649d60453", "eventType": "AwsApiCall", "recipientAccountId": "200000000000", "vpcEndpointId": "vpce-8******6" }